|
|
 |
Enhancing and Controlling Security |
| Your passport to security |
 |
|
 |
 |
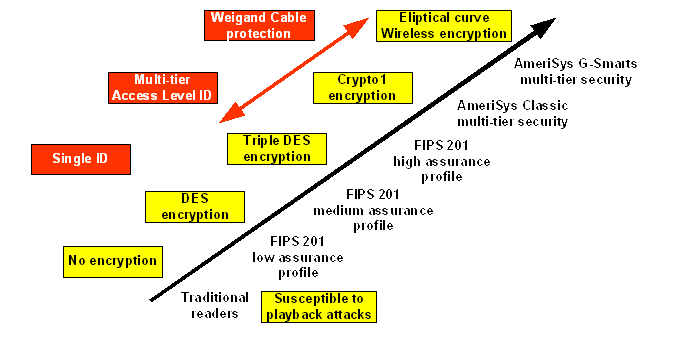
Beyond FIPS-140 and FIPS-201
Traditional access control cards are read-only, playback devices. When read, they simply send a fixed sequence, much
like a bar code. With the right equipment, one may record the sequence and play it back. Traditional access control
readers are susceptible to playback attacks.
|
|
AmeriSys devices are safer, they have means to thwart playback attack threats.
|
|
What is purported to be new technology, such as FIPS-140 and FIPS-201, is actually following into AmeriSys'
footsteps whereby the authentification challenge/response varies to prevent replay attacks.
|
As per FIPS-140 and FIPS-201 definitions,
classic AmeriSys readers and cards are classified as
High Assurance Profile.
|
|
FIPS-140 and FIPS-201, mandate encryption in both cards and readers using site-specific keys
in their high assurance profile... exactly what AmeriSys has been doing for almost a decade now!
|
|
AmeriSys devices are secure, they protect the cardholder's identity.
|
|
The AmeriSys Proximity Smart Card systems are the first commercially available Smart Cards and readers
that incorporate means to protect a cardholder's identity, over and above that specified in
the FIPS-201 Low Assurance Profile, FIPS-201 Medium Assurance Profile and FIPS-201 High Assurance
Profile. |
 Traditional access control cards will gladly spill their entire contents to any compatible reader they encounter.
Just pass by with your card and the reader will gladly reveal the entire contents of that card.
Traditional access control cards will gladly spill their entire contents to any compatible reader they encounter.
Just pass by with your card and the reader will gladly reveal the entire contents of that card.
|
|
AmeriSys Proximity Smart Card systems resolve this problem.
|
|
AmeriSys access control cards only reveal portions of their contents, and then, only to authorized
readers and only on a confirmed need-to-know basis. |
|
AmeriSys' modern, secure, micro-controller based readers, such as our G-Smarts reader series, allow you to modify
operational parameters and to define the reader's behavior. This gives you final control over your readers, your cards,
the authentification as well as additional control on the access request process.
|
|
Copyright 2006, AmeriSys Inc. All rights reserved.
No part of this web site, including the text, photos or illustrations, may be reproduced or transmitted in any other form or by any means
(electronic, photocopying, recording or otherwise) for commercial use without the prior written permission of AmeriSys Inc. |
|


